Cybersecurity Solutions
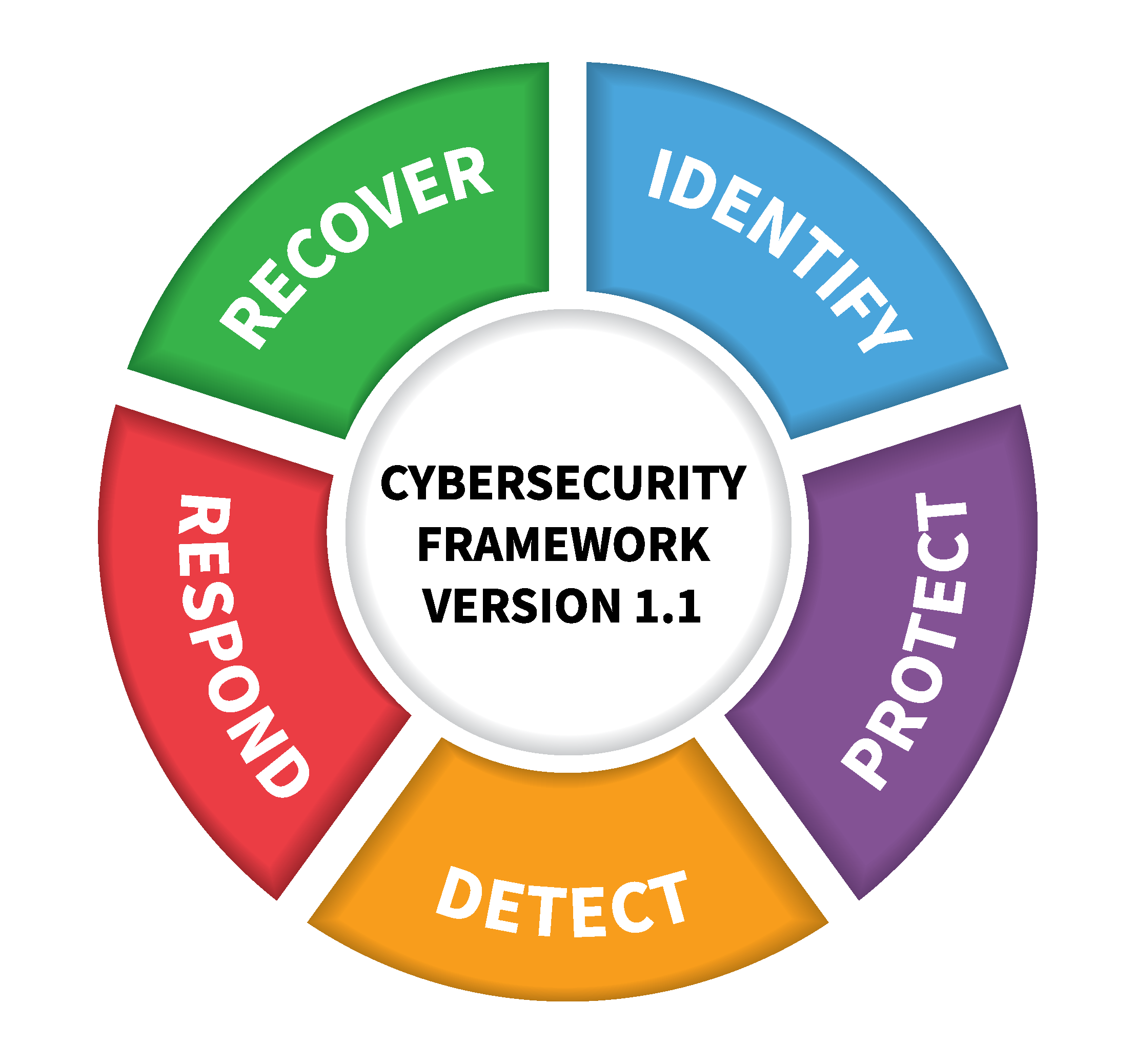
We provided tailored cybersecurity solutions and managed security services for complete coverage aligned with the NIST Cybersecurity Framework and the CIS Controls
Identify
Asset Management
CIS Control 1: Inventory and Control of Enterprise Assets
CIS Control 2: Inventory and Control of Software Assets
You can’t protect what you don’t know you have. Our discovery tools integrate with existing infrastructure to maintain an up-to-date inventory of hardware and software, while ensuring technology assets are controlled by appropriate management systems.
Data Protection
CIS Control 3: Data Protection
Whether your data lives in Microsoft 365, Google GSuite, Amazon AWS, or Mergers & Acquisitions have your data spread across multiple ecosystems, we’ll make sure you’re able to stay compliant and support the legal process by centralizing sensitive data classification, eDiscovery, legal holds, and audit logs.
Vendor Management
CIS Control 15: Service Provider Management
The 2013 Target breach was the first of many major cybersecurity incidents to illuminate risks introduced by 3rd party vendors. Most security and privacy regulations require the extension of data protection measures to 3rd party service providers. Our vendor risk management platform helps manage vendor risk, keeps track of 3rd party service providers, and facilitates automated audits to keep your organization in compliance.
Protect
Secure Configuration
CIS Control 4: Secure Configuration of Enterprise Assets and Software
Reduce your attack surface by hardening all of your technology platforms with secure configurations. Trusted secure configurations like the CIS Benchmarks reduce unnecessary risk exposure while helping to avoid misconfiguration vulnerabilities. In addition, the CIS Benchmarks map your endpoint configurations to common compliance frameworks.
Identity Management
CIS Control 5: Account Management
CIS Control 6: Access Control Management
Effective identity management keeps bad guys out while allowing your staff to do the jobs they’re authorized to do without hindrances. We’ll look at how your users access your systems and data, identify weaknesses, and deploy solutions to ensure best-practices are embedded in your workflow.
Vulnerability Management
CIS Control 7: Continous Vulnerability Management
CIS Control 12: Network Infrastructure Management
The prioritization and application of security updates across all network infrastructure is one of the most critical components of a security program. We can work with your IT team ensure that network infrastructure is managed and monitored, and automate existing patch management processes so updates are deployed as soon as possible with minimal interruption.
E-mail and Browser Protection
CIS Control 9: E-mail and Web Browser Protection
Enterprise e-mail platforms and modern web browsers have a variety of built-in security controls, but default configurations can leave your data exposed to potential threats. We'll harden the configuration of your e-mail platform, deploy protections against unsafe attachments and phishing attacks, and ensure web browsers are centrally managed.
Endpoint Protection
CIS Control 10: Malware Defense
We provide managed detection and response to swiftly and appropriately stop threats. Your systems will be continuously monitored for threats including malware, automated responses will block threats and prevent or minimize impact, and experts will use AI-driven analytics to conduct root cause analysis to aid in mitigation and prevention.
Security Awareness Training
CIS Control 14: Security Awareness and Skills Training
Despite sophisticated technical security controls, attack after attack succeed because an employee clicked on a single link in a phishing e-mail that made it through the filter. Our training platform trains your users how to protect themselves against cybersecurity threats, simulates phishing attacks, and identifies users or groups who may benefit from additional training.
Application Security
CIS Control 16: Application Software Security
Shift left. By embedding threat modelling into the design process, automating security testing, and empowering your dev teams with security champions, you can build more secure products while reducing development costs. Even if your organization doesn’t develop software, we’ll help you reduce supply chain risk by ensuring that your software vendors are using a secure development lifecycle.
Perimeter Protection
CIS Control 13: Network Monitoring and Defense
Today’s network perimeters extend beyond corporate facilities and datacenters - they extend to cloud applications, 3rd party vendor networks, and the home networks of your users. We’ll deploy and manage next-generation firewalls to protect your network traffic no matter where it flows.
Detect
Vulnerability Scanning
CIS Control 7: Continuous Vulnerability Management
Automated vulnerability scanning helps to identify vulnerabilities across your entire attack surface, and aids in the prioritization of mitigations. One-time scans are often a compliance requirement, but continuous monitoring and detection allows security teams to maintain complete visibility of the attack surface while ensuring mitigations are prioritized according to current threats and risk.
Offensive Operations
CIS Control 18: Penetration Testing
Offensive Operations such as penetration testing validate the effectiveness of your security by simulating an attack and exploiting weaknesses in your defenses. While vulnerability scanning identifies the existence of known weaknesses, penetration goes further by exploiting these weaknesses in order to determine potential impact to data or business processes. Offensive Operations are a core competency of JTI Cybersecurity. Click here to learn more.
Log Management and Analysis
CIS Control 8: Audit Log Management
Although often overlooked, audit logs are critical for both detection of malicious activity in-progress and forensic analysis following an attack. Even when audit logging is properly configured, they are rarely analyzed. We’ll ensure that all log sources are configured for central logging and analysis using an Security Incident and Event Management (SIEM) tool, and that audit data is reportable for both security operations and compliance.
Respond
Incident Response
CIS Control 17: Incident Response Management
We’ll work with you to establish an incident response program so your organization is prepared to quickly detect and respond to attacks. We can also provide advice and support to your augment your team when incidents occur.
Recover
Disaster Recovery and Business Continuity
CIS Control 11: Data Recovery
Information security’s CIA triad (Confidentiality, Integrity, and Availability) is an equilateral triangle, which means that maintaining availability of the data we protect is no less important than confidentiality or integrity. To ensure business continuity, backup systems need to be properly configured, maintained, and regularly tested. We provide hosted backup and disaster recovery solutions to protect data your data from accidental deletion or ransomware, and to reduce or eliminate downtime costs from hardware failures or natural disasters.
Cybersecurity for MSPs
"According to internal Microsoft Research, 90 percent of SMBs would consider hiring a new MSP if they offered the right cybersecurity solution,1 as most of them lack the skills inhouse to combat cyberattacks. By providing the security solutions your customers need, you can grow your business while protecting theirs."
We help MSPs build and maintain their customers’ confidence by augmenting their team with qualified and credentialed cybersecurity experts. We’ll both strengthen and simplify your approach to security by ensuring you have the tools and resources you need to protect your customers.